防火墙安全策略配置完,都是内网,IP能通端口不通是什么原因,服务器检查过了没有问题
- 0关注
- 0收藏,93浏览

1、防火墙web界面有个报文示踪功能可以模拟流经过设备的情况,将你业务流量写上去测试就可以看到是否是阻拦,用下面这个构造报文
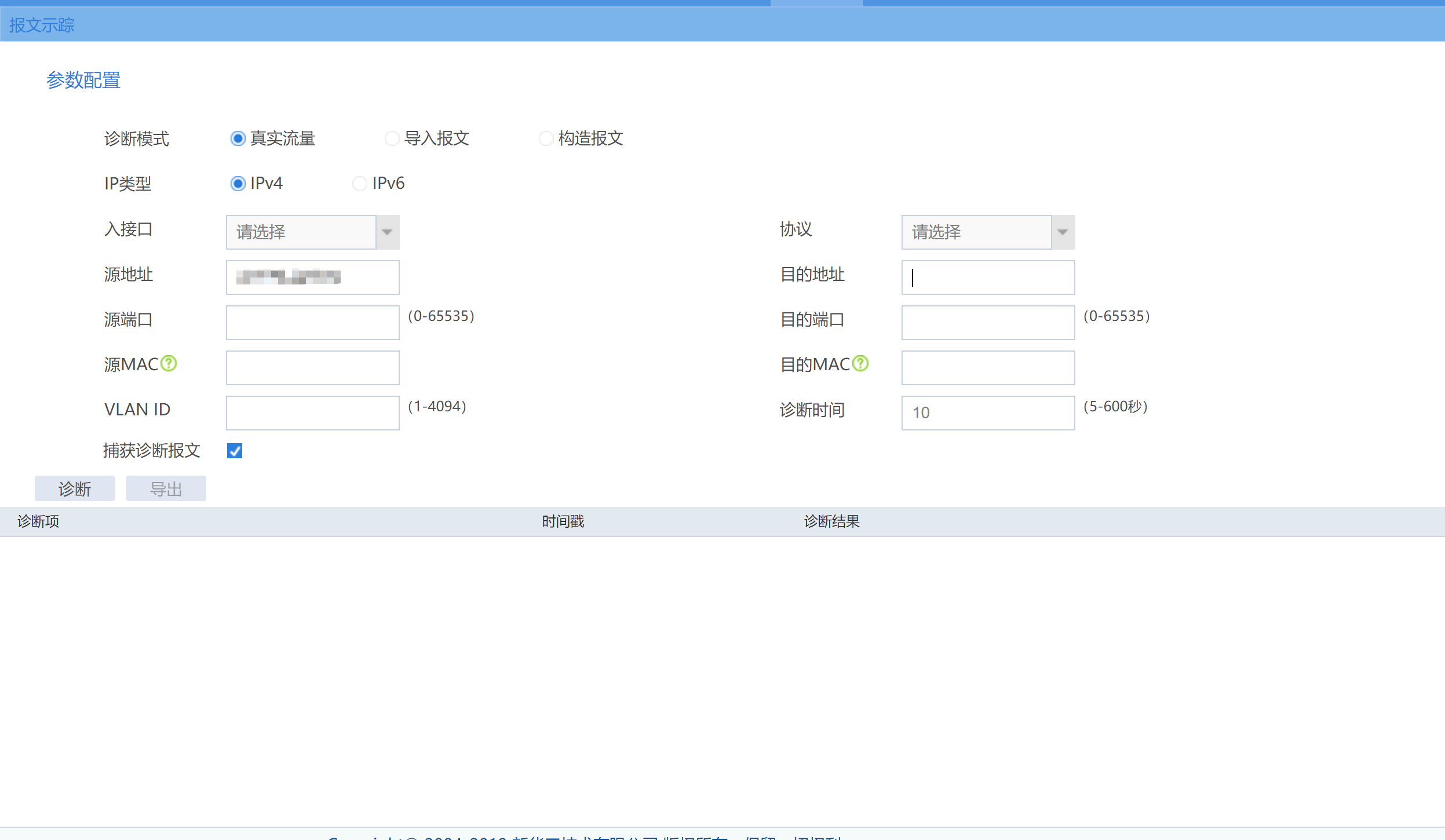
2、没web条件就用debug也可以定位
例:
#
acl advanced 3000
rule 0 permit icmp source 1.1.1.1 0 destination 2.2.2.2 0 //匹配去包
rule 5 permit icmp source 2.2.2.2 0 destination 1.1.1.1 0 //匹配回包
#
Acl里面写两条规则,匹配收发报文
开启debug,收集信息
<H3C>t m
The current terminal is enabled to display logs.
<H3C>t d
The current terminal is enabled to display debugging logs.
<H3C>debugging ip packet acl 3000
<H3C>debugging ip info acl 3000
<H3C>debugging security-policy packet ip acl 3000
<H3C>debugging aspf packet acl 3000
# version 7.1.064, Release 9323P15 # sysname FW # context Admin id 1 # telnet server enable # irf mac-address persistent timer irf auto-update enable undo irf link-delay irf member 1 priority 1 # security-zone intra-zone default permit # security-policy disable # dns server 211.138.24.66 # password-recovery enable # vlan 1 # vlan 10 # vlan 200 # object-group ip address 10.1.1.1 0 network host address 10.1.1.1 # object-group ip address 10.234.93.162 security-zone Local 0 network host address 10.234.93.162 # object-group ip address 192.168.46.36 security-zone Trust 0 network host address 192.168.46.36 # object-group ip address 慢病卫生院地址 0 network subnet 10.234.0.0 255.255.0.0 # object-group ip address 所有 0 network subnet 0.0.0.0 255.255.255.0 # object-group ip address 住院部1F 0 network subnet 192.168.31.0 255.255.255.0 # object-group service TCP_11111 0 service tcp destination eq 11111 # object-group service TCP_1521 0 service tcp destination eq 1521 # object-group service TCP_15400 0 service tcp destination eq 15400 # object-group service TCP_7631 0 service tcp destination eq 7631 # object-group service TCP_8010_8088 0 service tcp destination eq 8010 10 service tcp destination eq 8088 # object-group service TCP_8099 0 service tcp destination eq 8099 # object-group service TCP_8881-8884 0 service tcp destination range 8881 8884 # object-group service TCP_9010 0 service tcp destination eq 9010 # object-group service 防勒索端口 0 service tcp destination eq 445 10 service udp destination eq 445 20 service tcp destination eq 135 30 service udp destination eq 135 40 service tcp destination range 137 139 50 service udp destination range 137 139 # interface Bridge-Aggregation1 # interface NULL0 # interface Vlan-interface1 ip address 10.1.1.1 255.255.255.0 # interface Vlan-interface200 # interface GigabitEthernet1/0/0 port link-mode route ip address 192.168.0.1 255.255.255.0 # interface GigabitEthernet1/0/1 port link-mode route ip address 13.0.15.26 255.255.255.252 nat outbound 3002 # interface GigabitEthernet1/0/2 port link-mode route ip address 50.3.152.122 255.255.255.248 nat outbound 3001 # interface GigabitEthernet1/0/3 port link-mode route description 政务网 ip address 10.48.208.94 255.255.255.252 nat outbound 3004 # interface GigabitEthernet1/0/4 port link-mode route description 新政务网 ip address 172.17.41.18 255.255.255.252 nat outbound 3014 nat server protocol tcp global current-interface 7631 inside 192.168.46.31 7631 nat server protocol tcp global current-interface 8010 inside 192.168.46.14 8010 nat server protocol tcp global current-interface 8088 inside 192.168.46.14 8088 nat server protocol tcp global current-interface 8881 inside 192.168.46.29 8881 nat server protocol tcp global current-interface 8882 inside 192.168.46.29 8882 nat server protocol tcp global current-interface 8883 inside 192.168.46.29 8883 nat server protocol tcp global current-interface 8884 inside 192.168.46.29 8884 nat server protocol tcp global current-interface 11111 inside 192.168.46.31 11111 nat server protocol tcp global current-interface 15400 inside 192.168.46.29 15400 ipv6 address ::172.17.41.18/96 # interface GigabitEthernet1/0/5 port link-mode route description 远程会诊 ip address 10.104.75.2 255.255.255.0 nat outbound 3366 # interface GigabitEthernet1/0/6 port link-mode route description 云计算(医共体) nat outbound 3010 nat server protocol tcp global current-interface 1521 inside 192.168.46.25 1521 nat server protocol tcp global current-interface 3389 inside 192.168.48.111 3389 # interface GigabitEthernet1/0/7 port link-mode route ip address 10.234.93.162 255.255.255.224 nat outbound 3010 nat server protocol tcp global current-interface 8099 inside 192.168.46.36 8099 nat server protocol tcp global current-interface 9010 inside 192.168.46.36 9010 # interface GigabitEthernet1/0/12 port link-mode route # interface GigabitEthernet1/0/14 port link-mode route description 至老区 ip address 172.19.121.19 255.255.255.240 ip address 172.19.121.161 255.255.255.240 sub nat outbound 3003 # interface GigabitEthernet1/0/15 port link-mode route # interface GigabitEthernet1/0/16 port link-mode route # interface GigabitEthernet1/0/17 port link-mode route # interface GigabitEthernet1/0/18 port link-mode route # interface GigabitEthernet1/0/19 port link-mode route # interface GigabitEthernet1/0/20 port link-mode route # interface GigabitEthernet1/0/21 port link-mode route # interface GigabitEthernet1/0/8 port link-mode bridge # interface GigabitEthernet1/0/9 port link-mode bridge # interface GigabitEthernet1/0/10 port link-mode bridge # interface GigabitEthernet1/0/11 port link-mode bridge # interface GigabitEthernet1/0/13 port link-mode bridge port access vlan 10 # interface GigabitEthernet1/0/22 port link-mode bridge port link-aggregation group 1 # interface GigabitEthernet1/0/23 port link-mode bridge port link-aggregation group 1 # object-policy ip pass rule 0 pass # object-policy ip unntrust-trust # object-policy ip untrust-trust rule 0 pass source-ip 10.1.1.1 # security-zone name Local # security-zone name Trust import interface GigabitEthernet1/0/14 import interface Vlan-interface1 import interface Vlan-interface200 import interface GigabitEthernet1/0/8 vlan 1 import interface GigabitEthernet1/0/9 vlan 1 import interface GigabitEthernet1/0/10 vlan 1 import interface GigabitEthernet1/0/11 vlan 1 import interface GigabitEthernet1/0/13 vlan 10 import interface GigabitEthernet1/0/22 vlan 1 import interface GigabitEthernet1/0/23 vlan 1 # security-zone name DMZ # security-zone name Untrust import interface GigabitEthernet1/0/1 import interface GigabitEthernet1/0/2 import interface GigabitEthernet1/0/3 import interface GigabitEthernet1/0/4 import interface GigabitEthernet1/0/5 import interface GigabitEthernet1/0/6 import interface GigabitEthernet1/0/7 # security-zone name Management import interface GigabitEthernet1/0/0 # zone-pair security source Local destination Any object-policy apply ip pass # zone-pair security source Trust destination Local object-policy apply ip pass # zone-pair security source Trust destination Untrust object-policy apply ip pass # zone-pair security source Untrust destination Local object-policy apply ip pass # zone-pair security source Untrust destination Trust object-policy apply ip untrust-trust # scheduler logfile size 16 # line class aux user-role network-operator # line class console authentication-mode scheme user-role network-admin # line class vty user-role network-operator # line aux 0 user-role network-admin # line con 0 user-role network-admin # line vty 0 63 authentication-mode scheme user-role network-admin # ip route-static 10.82.161.148 32 172.19.121.30 description TO_ATM ip route-static 10.82.164.131 32 172.19.121.30 description 医保 ip route-static 10.85.96.0 24 172.19.121.30 ip route-static 10.85.200.0 24 172.19.121.30 ip route-static 10.85.200.99 32 172.19.121.30 ip route-static 10.85.254.0 24 172.19.121.30 ip route-static 10.100.6.0 24 10.104.75.1 description 远程会诊 ip route-static 10.100.12.112 28 10.104.75.1 description 远程会诊 ip route-static 10.120.6.0 24 172.19.121.30 ip route-static 10.120.13.0 24 172.19.121.30 ip route-static 10.120.84.0 24 172.19.121.30 ip route-static 10.123.128.0 24 172.19.121.30 ip route-static 10.123.130.100 32 172.19.121.30 ip route-static 10.234.0.0 16 10.234.93.161 description 云计算(医供体) ip route-static 10.234.93.0 24 10.234.93.161 description 云计算(医供体) ip route-static 13.0.0.0 8 13.0.15.25 ip route-static 13.0.7.0 24 172.19.121.30 ip route-static 50.0.0.0 8 50.3.152.121 ip route-static 59.207.0.0 16 172.17.41.17 ip route-static 59.227.152.0 24 172.17.41.17 ip route-static 59.227.154.0 24 172.17.41.17 ip route-static 59.227.155.0 24 172.17.41.17 ip route-static 59.227.157.0 24 172.17.41.17 ip route-static 59.227.159.0 24 172.17.41.17 ip route-static 59.227.172.0 24 172.17.41.17 ip route-static 59.255.31.64 28 172.17.41.17 ip route-static 59.255.152.8 32 172.17.41.17 ip route-static 172.19.0.0 24 172.19.121.30 description 退费 ip route-static 172.19.121.0 24 172.19.121.29 ip route-static 172.19.239.92 30 172.19.121.29 description 县人们医院监控平台 ip route-static 172.20.1.0 24 172.17.41.17 description 卫健委政务云 ip route-static 192.168.0.0 16 10.1.1.254 ip route-static 192.168.3.0 24 172.19.121.29 ip route-static 192.168.10.0 24 172.19.121.29 # ssh server enable # acl advanced 3001 rule 0 permit ip source 192.168.21.20 0 rule 5 permit ip source 192.168.21.21 0 rule 10 permit ip source 192.168.21.22 0 rule 15 permit ip source 192.168.21.23 0 rule 20 permit ip source 192.168.21.24 0 rule 25 permit ip source 192.168.21.25 0 rule 26 permit ip source 192.168.31.7 0 rule 30 permit ip source 192.168.31.25 0 rule 35 permit ip source 192.168.31.24 0 rule 40 permit ip source 192.168.31.23 0 rule 45 permit ip source 192.168.31.22 0 rule 50 permit ip source 192.168.31.21 0 rule 55 permit ip source 192.168.31.20 0 rule 56 permit ip source 192.168.34.31 0 rule 57 permit ip source 192.168.57.80 0 rule 60 deny ip # acl advanced 3002 rule 0 permit ip source 192.168.21.26 0 rule 5 permit ip source 192.168.21.27 0 rule 10 permit ip source 192.168.21.28 0 rule 15 permit ip source 192.168.21.29 0 rule 20 permit ip source 192.168.21.30 0 rule 25 permit ip source 192.168.31.26 0 rule 30 permit ip source 192.168.31.27 0 rule 35 permit ip source 192.168.31.28 0 rule 40 permit ip source 192.168.31.29 0 rule 45 permit ip source 192.168.31.30 0 rule 50 permit ip source 192.168.31.7 0 rule 55 permit ip source 192.168.57.80 0 rule 200 deny ip # acl advanced 3003 rule 11 deny ip destination 192.168.10.0 0.0.0.255 rule 12 deny ip destination 192.168.3.0 0.0.0.255 rule 13 deny ip destination 172.19.121.0 0.0.0.16 rule 30 permit ip # acl advanced 3004 rule 0 permit ip source 192.168.16.32 0 rule 5 permit ip source 192.168.16.0 0.0.0.255 rule 10 permit ip source 192.168.33.34 0 rule 15 permit ip source 172.19.121.25 0 rule 20 permit ip source 192.168.46.29 0 rule 25 permit ip source 192.168.57.80 0 # acl advanced 3010 rule 0 permit ip rule 5 permit ip source 192.168.46.25 0 rule 10 permit ip source 192.168.46.36 0 rule 15 permit ip source 192.168.57.80 0 rule 20 permit ip source 192.168.48.111 0 # acl advanced 3014 rule 0 permit ip source 192.168.16.32 0 rule 5 permit ip source 192.168.16.0 0.0.0.255 rule 10 permit ip source 192.168.33.34 0 rule 15 permit ip source 172.19.121.25 0 rule 20 permit ip source 192.168.46.14 0 rule 25 permit ip source 192.168.32.121 0 rule 30 permit ip source 192.168.21.55 0 rule 35 permit ip source 192.168.21.24 0 rule 40 permit ip source 192.168.21.26 0 rule 45 permit ip source 192.168.46.28 0 rule 50 permit ip source 192.168.21.0 0.0.0.255 rule 55 permit ip source 192.168.22.0 0.0.0.255 rule 60 permit ip source 192.168.23.0 0.0.0.255 rule 65 permit ip source 192.168.24.0 0.0.0.255 rule 70 permit ip source 192.168.10.0 0.0.0.255 rule 75 permit ip source 192.168.32.0 0.0.0.255 rule 80 permit ip source 192.168.46.29 0 rule 85 permit ip source 192.168.46.31 0 rule 90 permit ip source 192.168.46.39 0 rule 95 permit ip source 192.168.57.80 0 rule 100 permit ip source 192.168.46.33 0 rule 105 permit ip # acl advanced 3020 rule 0 permit ip source 192.168.46.25 0 # acl advanced 3111 rule 0 permit ip source 192.168.16.166 0 # acl advanced 3366 rule 0 permit ip source 192.168.31.0 0.0.0.255 rule 5 permit ip source 192.168.57.80 0 # acl advanced 3500 rule 0 permit ip source 10.1.2.0 0.0.0.255 # domain system # aaa session-limit ftp 16 aaa session-limit telnet 16 aaa session-limit ssh 16 domain default enable system # role name level-0 description Predefined level-0 role # role name level-1 description Predefined level-1 role # role name level-2 description Predefined level-2 role # role name level-3 description Predefined level-3 role # role name level-4 description Predefined level-4 role # role name level-5 description Predefined level-5 role # role name level-6 description Predefined level-6 role # role name level-7 description Predefined level-7 role # role name level-8 description Predefined level-8 role # role name level-9 description Predefined level-9 role # role name level-10 description Predefined level-10 role # role name level-11 description Predefined level-11 role # role name level-12 description Predefined level-12 role # role name level-13 description Predefined level-13 role # role name level-14 description Predefined level-14 role # user-group system # local-user Any class manage authorization-attribute user-role network-operator # local-user admin class manage password hash $h$6$R07DmAKInkWF5fS3$OG04VTlgGBf0c0eQXjbS9eJSQxO/tAxwwqQipYhm2odgQECYCQEosqsfZPqI2Fsr3NFVNmybBdWCYOlqMlKo4g== service-type ssh telnet terminal http https authorization-attribute user-role level-3 authorization-attribute user-role level-15 authorization-attribute user-role network-admin authorization-attribute user-role network-operator # session statistics enable # ip http enable ip https enable webui log enable # app-profile 0_IPv4 ips apply policy default mode protect anti-virus apply policy default mode protect # uapp-control # security-policy ip rule 1 name 防勒索 logging enable counting enable source-zone Trust source-zone DMZ source-zone Untrust destination-zone Trust destination-zone DMZ destination-zone Untrust service 防勒索端口 rule 0 name any action pass logging enable counting enable profile 0_IPv4 source-zone Local source-zone Trust destination-zone Local destination-zone Trust source-ip 所有 destination-ip 所有 rule 2 name 放行网络协议 action pass logging enable counting enable source-zone Trust source-zone Untrust source-zone Local destination-zone Local destination-zone Trust destination-zone Untrust source-ip 所有 destination-ip 所有 rule 3 name 慢病test action pass disable counting enable source-zone Untrust destination-zone Local source-ip 慢病卫生院地址 destination-ip 10.234.93.162 service TCP_8099 service TCP_9010 rule 4 name 慢病test2 action pass disable counting enable source-zone Local destination-zone Trust source-ip 所有 destination-ip 192.168.46.36 service TCP_8099 service TCP_9010 # return 这是配置文件
墙太老了,有个报文捕获,设备型号f1000-s-g2
编辑答案


亲~登录后才可以操作哦!
确定你的邮箱还未认证,请认证邮箱或绑定手机后进行当前操作
举报
×
侵犯我的权益
×
侵犯了我企业的权益
×
- 1. 您举报的内容是什么?(请在邮件中列出您举报的内容和链接地址)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
- 3. 是哪家企业?(营业执照,单位登记证明等证件)
- 4. 您与该企业的关系是?(您是企业法人或被授权人,需提供企业委托授权书)
抄袭了我的内容
×
原文链接或出处
诽谤我
×
- 1. 您举报的内容以及侵犯了您什么权益?(请在邮件中列出您举报的内容、链接地址,并给出简短的说明)
- 2. 您是谁?(身份证明材料,可以是身份证或护照等证件)
对根叔社区有害的内容
×
不规范转载
×
举报说明





看防火墙日志,有没有流量放行